There are a few tips we can provide when interpreting access assignments. First off, you need to understand the scope of the assignment – that is, is it at the management group, subscription group, resource group, or resource level?
Next, you can have a look at the role rules; in order to do this, you need to do the following:
- Navigate to the Azure portal by opening a web browser and browsing to https://portal.azure.com.
- Select Resource groups on the left, which will show all the current resource groups, and select a resource group in your subscription (in my case, it will be Az-104).
- Under Access control (IAM), choose Role assignments and select a role you want to have a look at in detail:
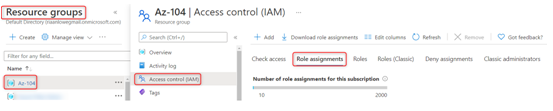
Figure 2.22 – The Role assignments section under the Access control (IAM) blade for a resource group
- In my case, I’m going to select the Contributor role:
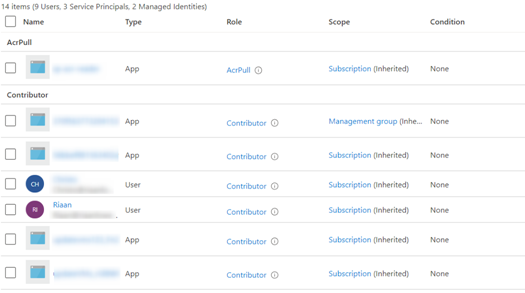
Figure 2.23 – The available role assignments
- Click on JSON; now, we will be able to view what the role has access to and also what actions are not allowed:
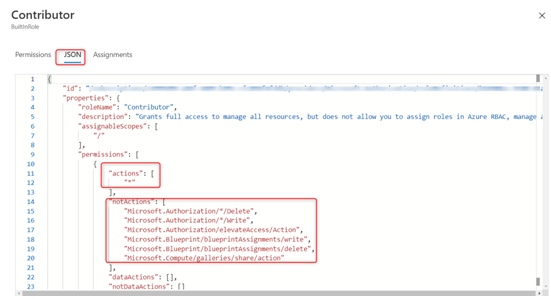
Figure 2.24 – JSON notation of the Contributor role
Tip
NotActions always take preference over Action items.
In this section, we discussed how to interpret role assignments by viewing the JSON format for a specific role.
We encourage you to read further by using the following links, which go into more detail about custom RBAC:
• https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles-template
• https://docs.microsoft.com/en-us/azure/role-based-access-control/role-assignments-list-portal
Summary
In this chapter, we discussed what custom roles are, how they work within Azure, and the different scope levels to which RBAC can be applied. We also created a custom RBAC role that only allows a user to restart a VM and not stop it. Finally, we went over how to interpret RBAC role assignments within the Azure portal.
In the next chapter, we’ll cover managing subscriptions and governance.