Let’s go ahead and use the Azure portal to create a custom RBAC role from scratch named IT Support – Restart VMs only, which can only restart virtual machines and deny the startup and shutdown of them:
- Navigate to the Azure portal by opening a web browser and browsing to https://portal.azure.com.
- In the top section search bar, search for and select Subscriptions:
Figure 2.2 – The search bar in Azure
- Select an active subscription; in my case, this will be the Demo subscription, as seen in the following screenshot:
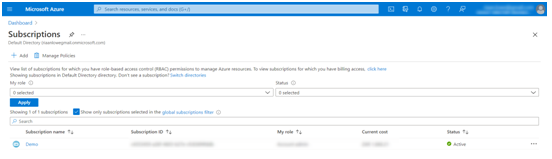
Figure 2.3 – A display of all subscriptions available
- Select Access control (IAM), click on Add, and select Add custom role:
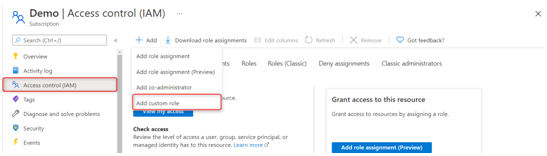
Figure 2.4 – The Access control (IAM) blade for a selected subscription
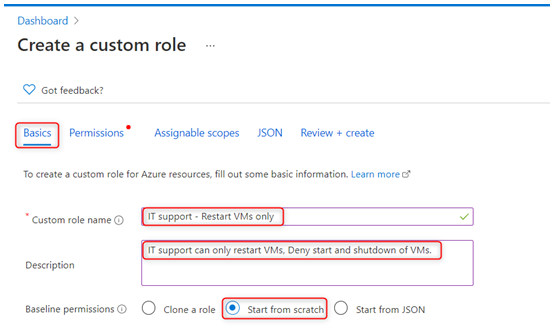
Figure 2.5 – The custom role creation blade
- Next, we need to specify the permissions. Click on the Add permissions button, and in the search bar that pops up, search for Virtual machines and select Microsoft ClassicCompute:
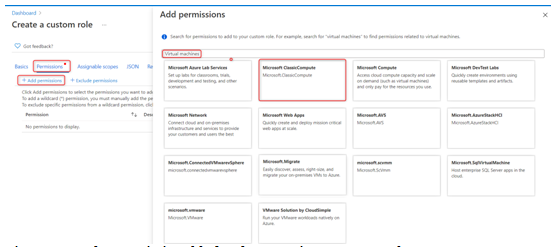
Figure 2.5 – The custom role creation blade
- Next, we need to specify the permissions. Click on the Add permissions button, and in the search bar that pops up, search for Virtual machines and select Microsoft ClassicCompute:
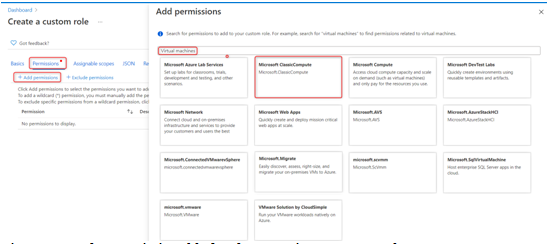
Figure 2.6 – The Permissions blade when creating a custom role
- A new blade will pop up with all the compute permissions. Scroll all the way down to Microsoft.Compute/virtualMachines and select Read: Get Virtual Machine and Other: Restart Virtual Machine, and then click Add:
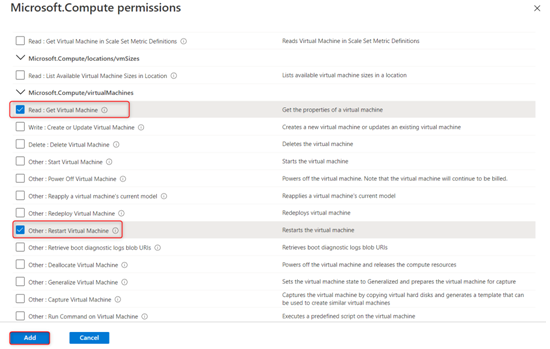
Figure 2.7 – The custom role creation permissions available for Microsoft.Compute
- Next, we need to exclude this role from starting and shutting down virtual machines. Click on the Exclude permissions button and search for Virtual machines again, and then select Microsoft Compute:
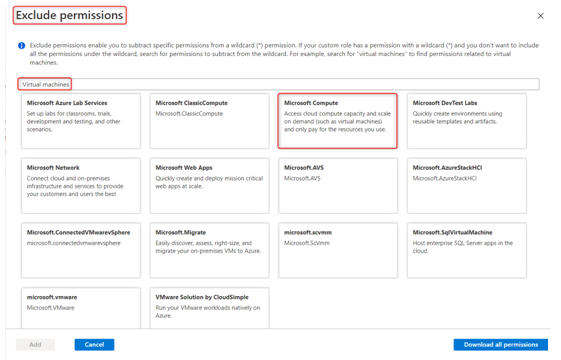
Figure 2.8 – Custom role exclusions when searching for virtual machines
- Go to Microsoft.Compute/virtualMachines and select Other: Start Virtual Machine and Other: Power Off Virtual Machine, and then click Add:
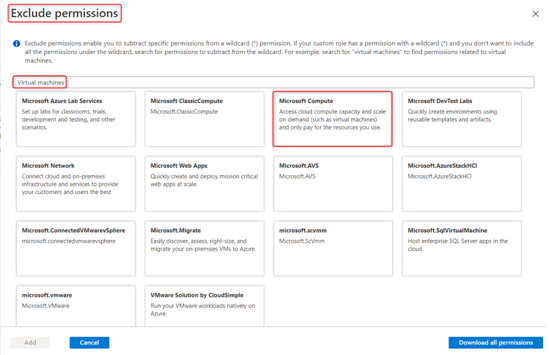
Figure 2.9 – The custom role exclusion list for Microsoft.Compute
- You will notice that the new role now has the following permission types:
o Action: Read the Virtual Machine (VM).
o Action: Restart the VM.
o NotAction: Start the VM.
o NotAction: Shut down the VM.
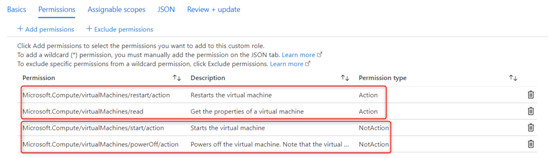
Figure 2.10 – A custom role permissions overview displaying Actions and NotActions
Tip
Actions are permission actions that are allowed; NotActions are permission actions that are specifically not allowed.
Click on Next.
- Next, we have Assignable scopes, where we can choose where this custom role will be available for assignment. In this scenario, we are going to leave it at the default subscription level that was automatically added and then click on Next:
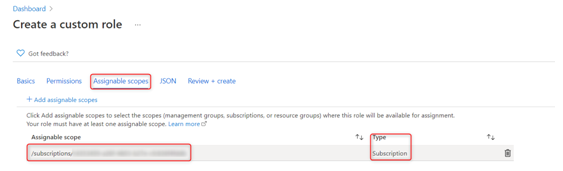
Figure 2.11 – The custom role assignable scopes
- Next, we have the JSON tab, which shows the permissions for the new role in JSON format; we also have the ability to download the JSON code. For now, let’s click on Next:
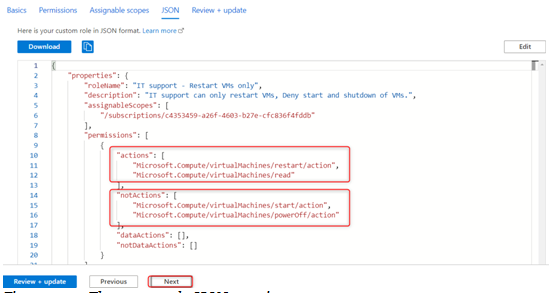
Figure 2.12 – The custom role JSON notation
- The last tab is the Review + update tab, which is a summary of our configuration; click on Create:
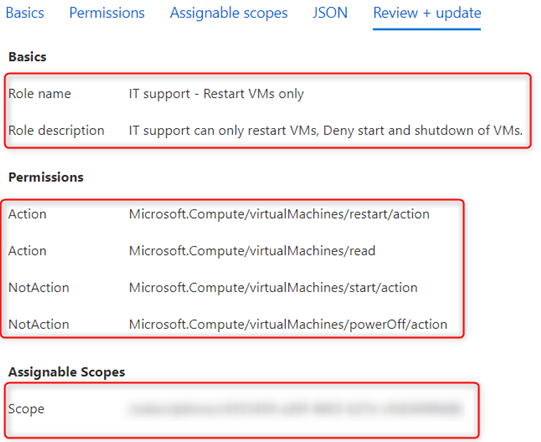
Figure 2.13 – The custom role review before creation
- A new pop-up window will appear, stating that the new custom role has been created and that we can start assigning the role as soon as replication has taken place, which is usually around 5 minutes or less.
In this section, we have created a custom RBAC role via the Azure portal from scratch, which only allows a VM to be restarted and blocks any start or shutdown attempts on a VM.
We encourage you to read up further by using the following links, which go into detail about Azure AD custom roles:
• https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles
• https://docs.microsoft.com/en-us/azure/active-directory/roles/custom-create
Important!
Students should be comfortable using the JSON format while creating a custom role.







